This self-paced course will help you prepare for the Azure Developer certification exam AZ-204: Developing Solutions for Microsoft Azure.


Container Security Tool – Aqua Security’s MicroScanner lets you check your container images for vulnerabilities. If your image has any known high-severity issue, MicroScanner can fail the image build, making it easy to include as a step in your CI/CD pipeline.

Container Security Tool – Aqua provides end-to-end security for applications running on Docker Enterprise Edition or Community Edition, protecting the DevOps pipeline and production workloads in runtime with full visibility and control.
With Aqua, you can protect your Docker applications running on either Linux (docker or container runtimes) or Windows, with powerful image assurance, container immutability, and least-privilege enforcement, and container firewall.
Login to the URL and then fill up the details on the page and then we will be getting an email and when we click on it we will get the full details like shown below :
https://microscanner.aquasec.com/signup
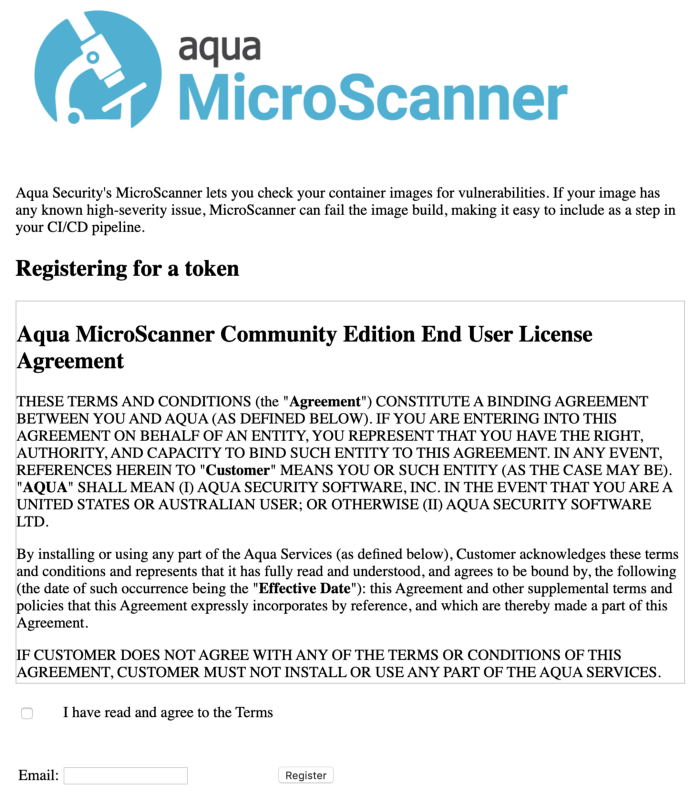
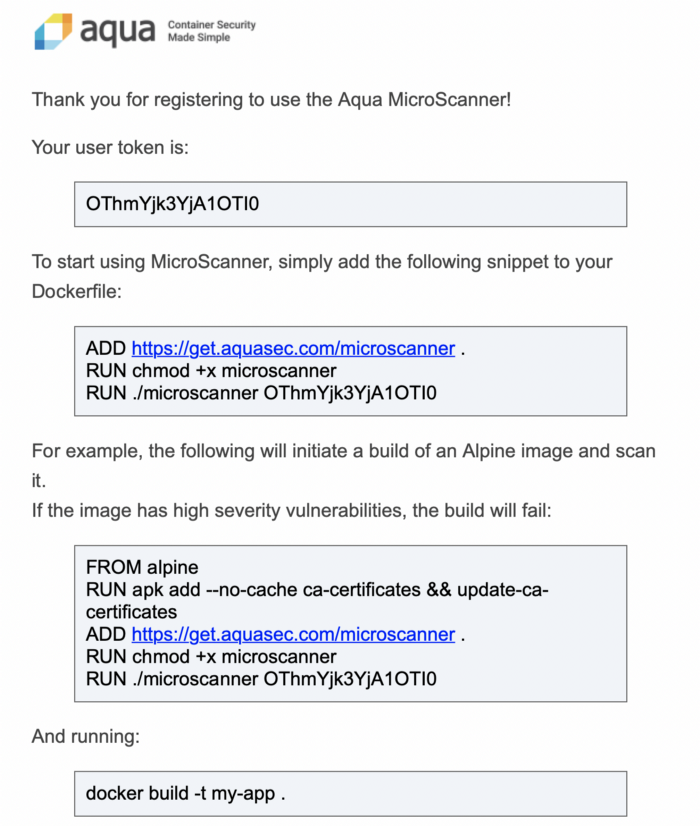
$ docker run --rm -it aquasec/microscanner --register <email address>
2. Adding microscanner to your Dockerfile
The following lines add microscanner to a Dockerfile, and execute it.
ADD https://get.aquasec.com/microscanner /
RUN chmod +x /microscanner
RUN /microscanner <TOKEN> [--continue-on-failure]
3. You may also need to add ca-certificates to the image if they are not already built into the parent image, or added in your Dockerfile so that micro scanner can make an HTTPS connection. For example (Debian):
RUN apt-get update && apt-get -y install ca-certificates
or (Alpine):
RUN apk add --no-cache ca-certificates && update-ca-certificates
4. Example Dockerfile
FROM debian:jessie-slim
RUN apt-get update && apt-get -y install ca-certificates
ADD https://get.aquasec.com/microscanner /
RUN chmod +x /microscanner
ARG token
RUN /microscanner ${token}
RUN echo "No vulnerabilities!"
Pass the token obtained on registration in at build time.
$ docker build --build-arg=token=<TOKEN> --no-cache .RUN apk add --no-cache ca-certificates && update-ca-certificates && \
wget -O /microscanner https://get.aquasec.com/microscanner && \
chmod +x /microscanner && \
/microscanner <token> && \
rm -rf /microscanner
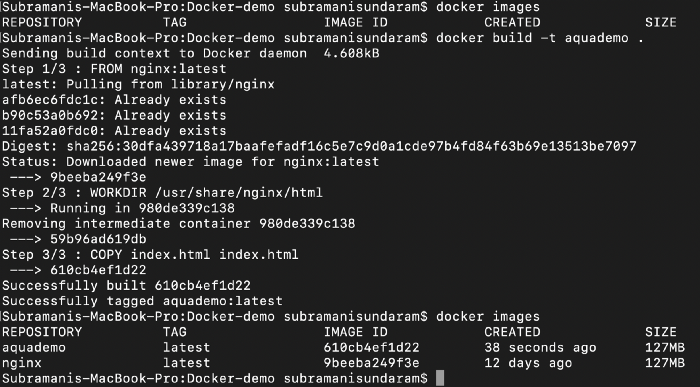
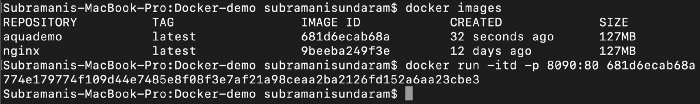
3. When we build this image we will get the image created such as below , we use this command to do it.
docker build -t <imagename> <location of the Dockerfile>
4. To run the docker image to see the output we need to port map it as the internal port of the image is tagged to the port 80 and the outer port we need to map it to the port which is available as 8090 or 8080 depending upon the free port available on the machine.

5. Now we can include the Aqua container scanner API key from the email which we received above.
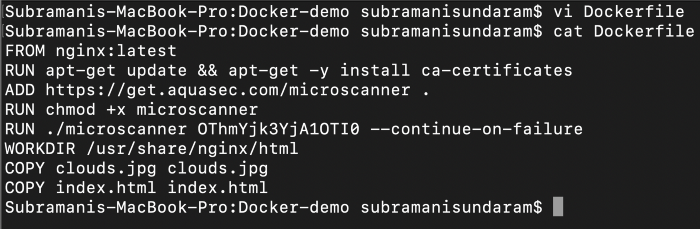
6. When we build this image we will get the image created such as below , we use this command to do it.
docker build -t <imagename> <location of the Dockerfile>
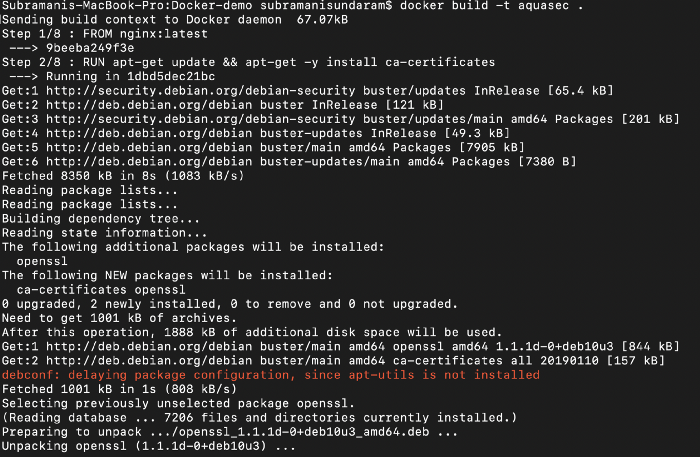
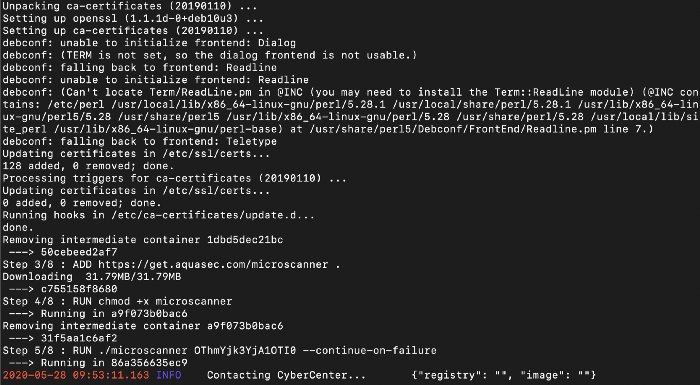
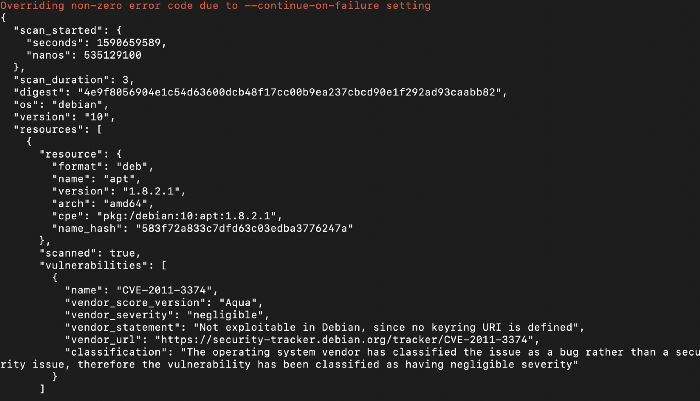
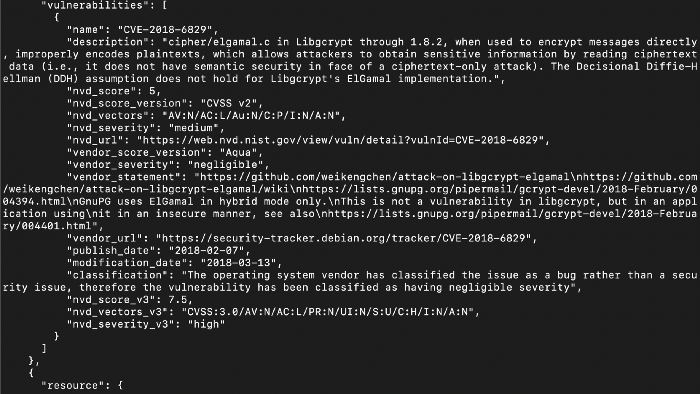
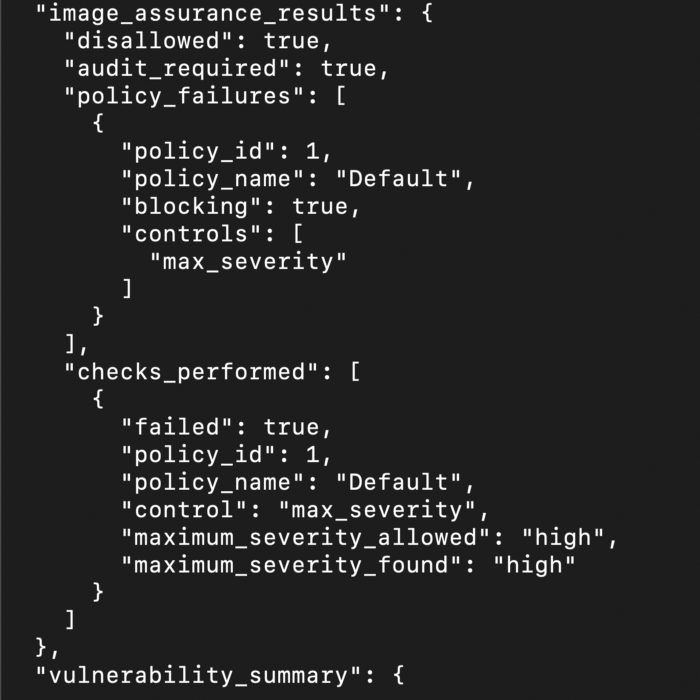
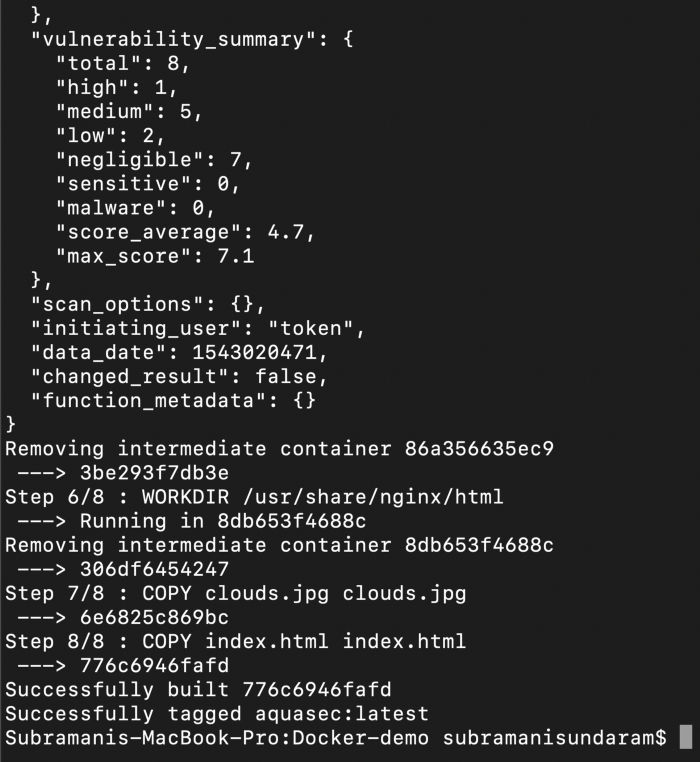
7. If we see the above the docker image while building it scans the complete image and then if tell us how many vulnerabilities are there and we can even define a condition that if there are any high vulnerability we can avoid to check-in the image into the registry.
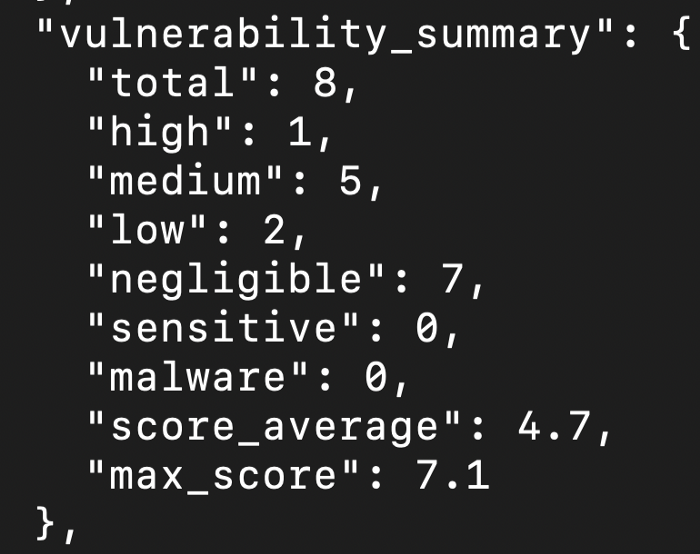
8. To run the docker image to see the output we need to port map it as the internal port of the image is tagged to the port 80 and the outer port we need to map it to the port which is available as 8090 or 8080 depending upon the free port available on the machine.
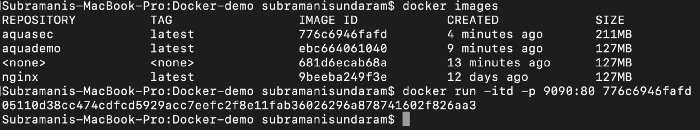

If we see the above, we are getting the same output as the before one, but this time the image that you are using is the SCANNED one, and if we find any faults we can remove it before even it comes to our section. That’s the advantage of this container security.

This self-paced course will help you prepare for the Azure Developer certification exam AZ-204: Developing Solutions for Microsoft Azure.